DarkBlue Intelligence Suite / Unmasking the Fentanyl Trade
March 11, 2025
ClickFix CAPTCHA Phishing: The Highly Effective Scam Technique Coming to a Dark Web Near You
A dangerously successful open-web attack vector that involves tricking users into downloading malware to complete CAPTCHAs is predicted to move to the dark web very soon. This development underscores the need for dark web threat intelligence and open source dark web monitoring to track emerging attack trends.
Looking to stay ahead of dark web threats? Get the latest in dark web news, OSINT tools, and more when you subscribe to the DarkBlue newsletter.
CAPTCHAS are being hijacked, and it’s very convincing
Anyone on the internet will be familiar with CAPTCHAs (short for Completely Automated Public Turing test to tell Computers and Humans Apart). They’re those little puzzles you’re often required to solve to gain access to a website or submit a form, typically involving typing out letters and numbers from an image to “prove you’re human.” Designed to weed out bots, CAPTCHAs have become ubiquitous on the open web, and most of us probably don’t think twice about completing them. However, threat actors have found a way to hijack the CAPTCHA system by replacing CAPTCHA pages with malicious duplicates.
Emerging in 2024, these “ClickFix” attacks are executed by threat actors who log into websites with stolen credentials and install plugins that display fake notifications to the user. When the user goes to complete the CAPTCHA on a seemingly harmless site—one they may have even safely visited many times before—fake notifications pop up warning the user that the webpage or document cannot be displayed correctly until they click the “Fix It” button and complete the steps. Following these prompts, the user installs what they believe to be a required update to complete the CAPTCHA, such as downloading an additional font. However, in reality, they have been socially engineered into willingly installing malware on their device.
What’s worse, because the user is actively participating in the installation, it becomes much easier for the malware to bypass web browser security features, such as Google Safe Browsing. The malware installed is often the worst kind: trojans that enable complete remote access to the device and infostealers like Vidar Stealer, DarkGate, and Lumma Stealer.
Variations on the ClickFix technique
One of the most insidious aspects of the ClickFix scam is that it can easily be recycled and modified to fit trends of the moment, making the social engineering aspect highly effective.
The fake Ross Ulbricht Telegram channel
In one recent example, threat actors on X exploited the explosive news surrounding the unexpected pardon of Silk Road founder, Ross Ulbricht. In this version, a fake but verified Ross Ulbricht X account directed users to join to a Telegram channel supposedly run by Ulbricht. Prior to joining, however, users had to complete a series of prompts for “verification” that tricked them into running PowerShell code that infected their devices with malware.
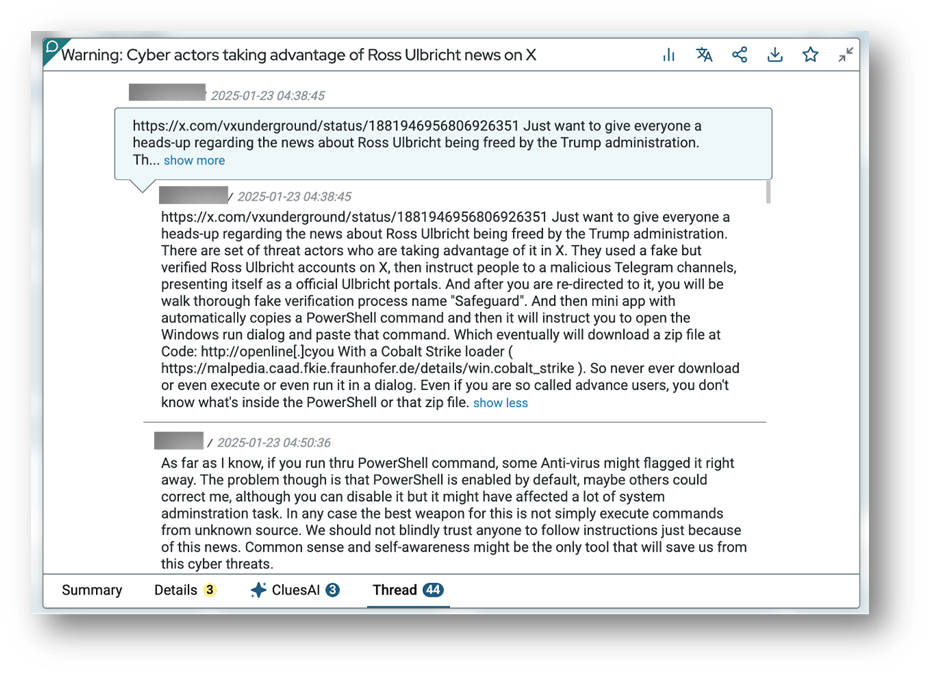
Figure 1: Screenshot of a recreation of X users discussion Ross Ulbricht attack vector, as captured in DarkBlue
How it works
- Attack Method: Users are led to a Telegram channel via fake but verified Ross Ulbricht accounts on X. Once on Telegram, they are met with an identity verification request named "Safeguard," which guides them through a fake verification process. At the end, a Telegram mini app displays a false verification dialog, automatically copying a PowerShell command to the clipboard and prompting the user to run it via the Windows Run dialog.
- Payload: The PowerShell script downloads and executes a ZIP file containing multiple files, including identity-helper.exe, which has been linked to a potential Cobalt Strike loader.
- Impact: Cobalt Strike is a penetration testing tool frequently abused by threat actors to gain remote access to systems, often preceding ransomware deployment and data theft.
- Evasion Techniques: The language used throughout the verification process is carefully selected to prevent raising suspicion and maintain the illusion of legitimacy.
Reminder: Users should never execute commands copied from online sources into their Windows Run dialog or PowerShell terminal unless they are certain of their legitimacy. If unsure, pasting copied content into a text editor for review can help identify obfuscation, which is often a red flag. But the safest defense is a secure virtual browser like DarkPursuit, which prevents malicious code from ever reaching your device.
The infostealer confounding even security experts
In another example, Lumma Stealer, a malware-as-a-service (MaaS) tool active since 2022, was designed to steal sensitive information such as cryptocurrency wallets, browser data, email credentials, and financial files.
In the campaign, the fake CAPTCHA presented instructions to open the Windows Run window by pressing Windows+R, paste the clipboard’s content in the run window using CTRL+V, and then press ENTER to execute it. Even users who are savvy enough to know not to download and run files on the web often did not realize what they were doing when they followed the instructions. Furthermore, downloading malware payloads outside the browser served an anti-analysis mechanism, evading browser-based cybersecurity controls.
How it works
- Attack Method: Victims are redirected to fake CAPTCHA pages that instruct them to execute commands via the Windows Run dialog. This triggers a PowerShell script that downloads and installs the malware.
- Targets: The campaign spans multiple industries, including healthcare, banking, telecom, and marketing, with victims in countries like Argentina, the U.S., and the Philippines.
- Capabilities: Lumma Stealer scans files for sensitive keywords (e.g., “wallet.txt”) and exfiltrates data to command-and-control servers. It also uses techniques like process hollowing and AMSI bypassing to evade detection.
- Distribution: Besides fake CAPTCHAs, it spreads via phishing emails, cracked software, Discord messages, and GitHub-hosted payloads.
Reminder: Users should avoid executing commands from untrusted sources and implement robust endpoint protection solutions. Lumma Stealer poses a significant risk of financial loss and identity theft due to its ability to steal critical data. Avoid risks like these by using a secure virtual machine, such as the DarkBlue Intelligence Suite’s DarkPursuit, when accessing unsafe online environments.
The expected move to the dark web
CACI analysts have not yet seen this attack vector move to the dark web, but it’s only a matter of time. Darknet market administrators have recently started inquiring about CAPTCHA methodologies, indicating that similar CAPTCHA scams are right around the corner. Once these techniques are weaponized for dark web marketplaces, they could be bundled with other phishing kits or sold as standalone attack tools, making them even more widespread. Dark web software used by cybercriminals is evolving rapidly, and monitoring these developments through dark web threat intelligence and open source dark web monitoring is critical for early detection.
Protecting against ClickFix attacks
To avoid falling victim to these attacks, users should be wary of CAPTCHA pages that require additional downloads or scripts. Security professionals should ensure their organizations have strong endpoint protections and browser security measures in place.
For those conducting investigative work in potentially compromised environments, secure virtual machines are a must. The DarkBlue Intelligence Suite’s DarkPursuit offers a secure research environment to analyze threats while minimizing exposure to malware and phishing attempts. As CAPTCHA phishing evolves, leveraging secure tools like DarkPursuit and OSINT best practices will be essential in staying ahead of threat actors. Request a free trial to test out DarkBlue today.